What is Identity and Access Management?
Identity and access management (IAM) is a security discipline that ensures the right individuals have access to the right resources at the right time as per their requirements.
IAM policies and controls ensure appropriate access across multiple applications, resources and in the cloud. IAM is a critical undertaking in an organization that aligns the business needs and ensures proper security.
Companies that develop mature IAM capabilities often reduce cost, reduce risk to the firm and improve customer satisfaction. This maturity can often be achieved via automation of identity and access management through various IGA (Identity Governance) solutions.
Two major components of Identity and Access Management include
Authentication
Authentication is something that validates the user’s identity ensuring the right person is gaining access to the systems. Authentication includes SSO (single-sign-on), MFA (Multi-factor authentication) etc.
Authorization
Authorization is something that ensures that users have appropriate types of access to the systems. Accurate authorizations can be done through RBAC (Role based access control) or ABAC (Attribute based access controls).
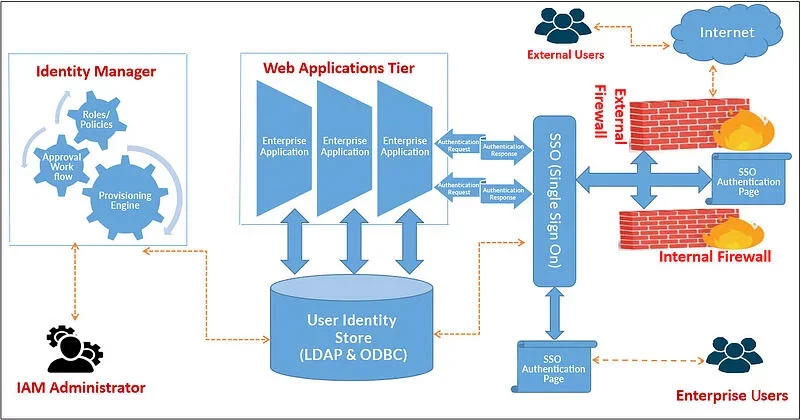
IAM Architecture
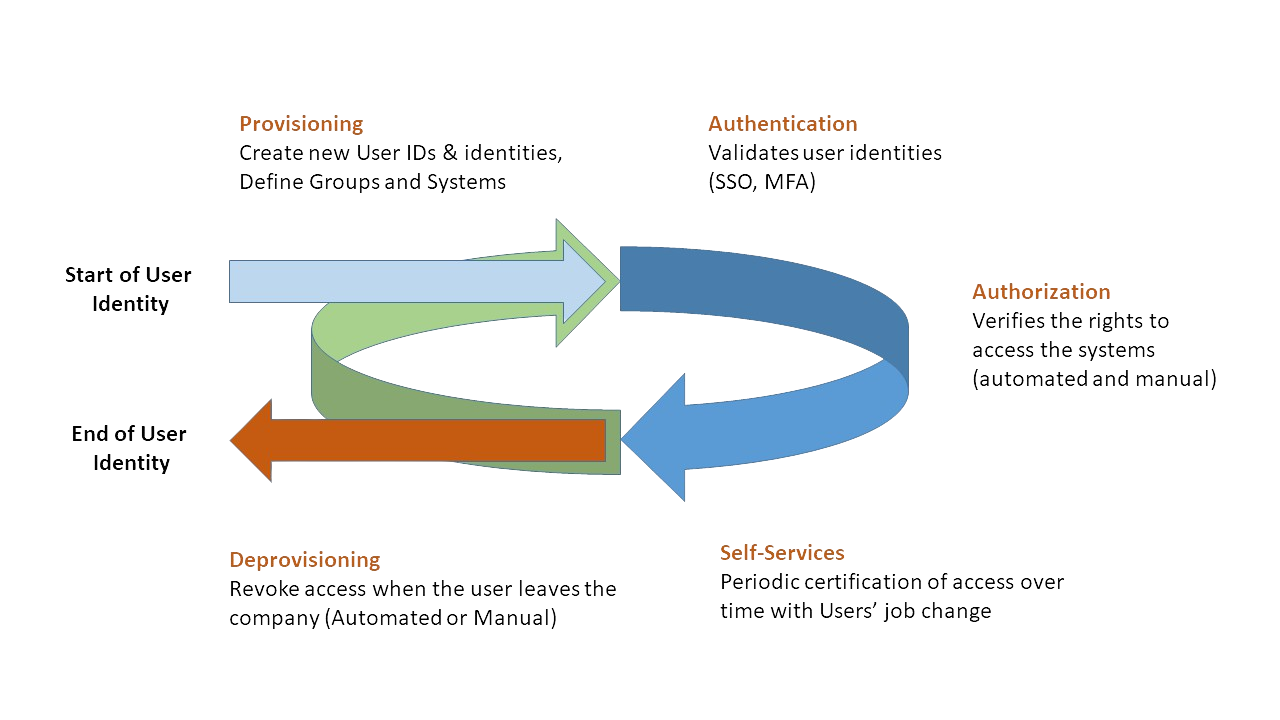
Identity and Access Management Lifecycle
Our Service Features
Identity and Access Management Strategy – Advisory on building and implementing organization wide IAM Strategy and IAM Programs
Core IAM/IGA Solution - Decision making, building and Implementing role-based access solutions
Privileged Access Management (PAM), MFA & Zero Trust – Analysis, remediation, implementing MFA and PAM solutions
Unstructured Data Governance – Remediation, Tool decision making and implementation of solutions
Cloud Identity and Access Management – Standardization of role-based access, secret key management and just-in-time access solutioning
Governance, Metrics and KPIs – Implementing key metrics and KPIs to ensure IAM program is in check to stay ahead of the curve
